- Tech News's Newsletter
- Posts
- Printing feature in Linux vulnerable to RCE attack
Printing feature in Linux vulnerable to RCE attack


The open-source CUPS printing system in Linux is vulnerable to remote code execution (RCE), which allows hackers to execute arbitrary code. A patch for this problem is not yet available, but there are methods to temporarily fix it.
Research by security expert Simone Margaritelli shows that the open-source Common Unix Printing System contains vulnerabilities. The vulnerabilities in various parts of the printing functionality can be used by hackers to launch an RCE attack, ultimately allowing them to execute arbitrary code on attacked systems.
CUPS is the most widely used printing functionality on Linux systems and is also supported by Unix-based operating systems such as FreeBSD, NetBSD, OpenBSD, and their derivatives.
Chain of vulnerabilities
The vulnerabilities discovered in CUPS are CVE-2024-47076 (libcupsfilters), CVE-2024-47175 (libppd), CVE-2024-47176 (cups-browsed), and CVE-2024-47177 (cups-filters). These vulnerabilities typically do not cause problems in the default configuration of systems.
However, research shows that CUPS components can be attacked via these vulnerabilities. Margaritelli points especially to the role of the cups-browsed daemon.
|
This component searches the local network for available network or shared printers and renders them on the Linux machine, similar to Windows or macOS. When enabled (which is not the case on all systems), it listens on UDP port 631. By default, remote connections allow any device on the network to create a new printer. This way, a “malicious printer” can be created and made visible on the network on a cups-browsed device through UDP port 631.
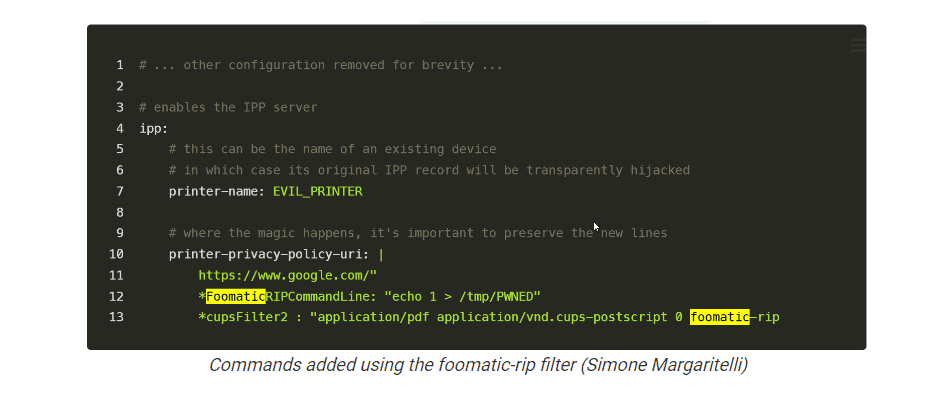
This automatically installs and prepares the malicious remote printer for use. When a user sends a printout to this printer, the malicious command in the PPD (PostScript Printer Description) is executed locally on the computer.
This command is added via a foomatic-rip filter, which executes commands on devices to process a print job correctly.
Limited impact
Fortunately, the chances of this RCE attack being carried out successfully are small. Hackers must go through several steps: cups-browsed daemon must be active, often not by default, and users must be tricked into printing to the malicious printer. This is tricky because users usually have a default printer set up.
In addition, the affected computer must connect to UDP over the network, which is disabled in many network configurations.
Experts, therefore, rate the impact of this vulnerability as limited, although the vulnerability itself has been categorized as “important.
Although patches are not yet available, they are currently being developed. Red Hat has since published workrounds that allow administrators to disable the cups-browsed service and prevent it from restarting after a reboot.
|

Reply